Free
Absolutely Free
osquery overview
osquery uses basic SQL commands to leverage a relational data-model to describe a device.
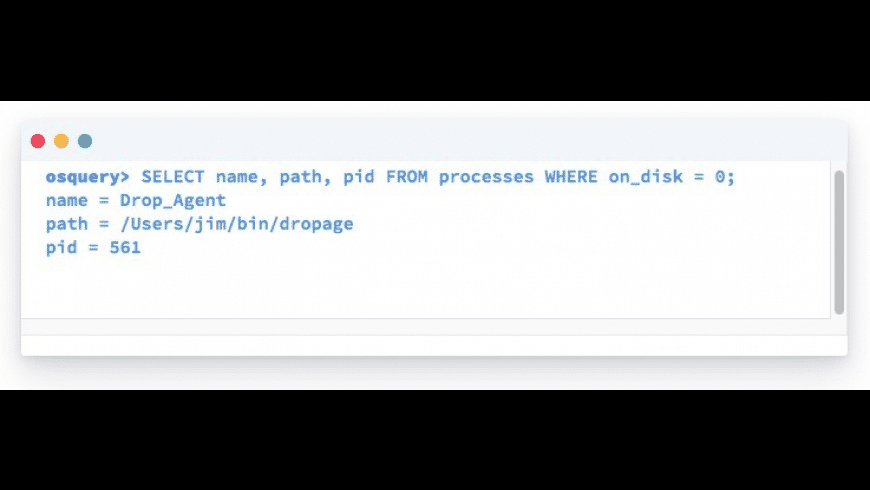
Processes running without a binary on disk
Frequently, attackers will leave a malicious process running but delete the original binary on disk. This query returns any process whose original binary has been deleted, which could be an indicator of a suspicious process.
Three things you should know about osquery
- It's fast and tested: Our build infrastructure ensures that newly introduced code is benchmarked and tested. We perform continuous testing for memory leaks, thread safety, and binary reproducibility on all supported platforms.
- It runs everywhere: Windows, macOS, CentOS, FreeBSD, and almost every Linux OS released since 2011 are supported with no dependencies. osquery powers some of the most demanding companies, including Facebook.
- It's open source: Osquery is released under the Apache License. Ever since we open-sourced it in 2014, organizations and individuals have contributed an ever-growing list of impressive features, useful tools, and helpful documentation.
What’s new in version 5.11
Updated on Feb 01 2024
Bug Fixes
- Add stricter checks to JSON parsing (#8229)
- Fix signed/unsigned mismatch in powershell_events (#8225)
- Fix a crash in firefox_addons (#8227)
- Correct the aws_sts_region behavior (#8184)
Full list of changes available here
Information
App requirements
- Intel 64
- Apple Silicon
- OS X 10.9 or later
Try our new feature and write a detailed review about osquery. All reviews will be posted soon.
(0 Reviews of )
There are no reviews yet
Comments
User Ratings
May 3 2023
Version: 5.8.2
I finally found a use for OSQUERY. Or perhaps I should say, found a product that uses it: Vanta.
Vanta is a SOC 2 compliance tool that once installed on a workstation, monitors for "un-binaried" processes (processes for which there isn't an app; malware) and other items that may raises suspicions. Vanta is effectively spyware, so I'd only put it on company-provided hardware, and there isn't (to my knowledge) any end-user purpose. Still, OSQUERY is the basis for how Vanta works. There may be some applicability for geeky types who wish to dig into the innards of their macOS.
Help the community
There are no ratings yet, be the first to leave one
Free
Absolutely Free
Similar apps
RazorSQL
Manage multiple databases from a single application.
Is this app is similar to RazorSQL? Vote to improve the quality of this list.
Vote results
1
Upvotes
1
Total score
0
Downvotes
DtSQL
Universal database query and editor tool.
Is this app is similar to DtSQL? Vote to improve the quality of this list.
Vote results
1
Upvotes
1
Total score
0
Downvotes
New and Recently Updated